By Val Vask, CISSP & Cybersecurity Expert
According to IoT Analytics, the rapid growth of IoT devices (approximately 16.6 billion in 2023), reached 18.8 billion in 2024. If we follow the current trend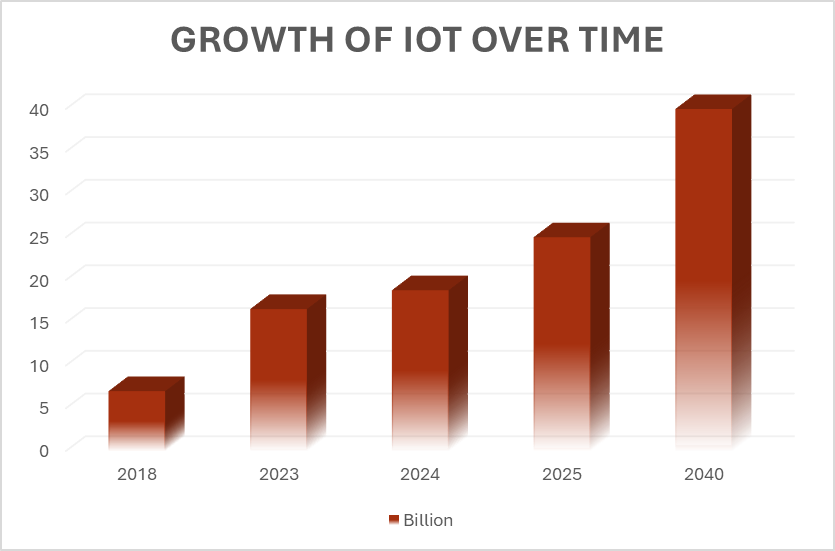 , the deployment of IoT devices should reach at least 21.2 billion in 2025 but is expected to grow to as high as 25 million, which introduces significant security challenges to small and medium-sized business (SMBs), as well as large businesses. Unlike traditional IT systems, IoT devices often lack robust security controls, creating an expanded attack surface. Many organizations struggle to maintain an accurate inventory of connected devices, leaving them vulnerable to exploitation. Furthermore, automated patching of IoT devices remains difficult in an enterprise environment. This means that the more devices connected without proper security, the greater the risk of breaches. When you consider the fact that most of these devices are connected to the corporate network, the probability of a major breach increases.
, the deployment of IoT devices should reach at least 21.2 billion in 2025 but is expected to grow to as high as 25 million, which introduces significant security challenges to small and medium-sized business (SMBs), as well as large businesses. Unlike traditional IT systems, IoT devices often lack robust security controls, creating an expanded attack surface. Many organizations struggle to maintain an accurate inventory of connected devices, leaving them vulnerable to exploitation. Furthermore, automated patching of IoT devices remains difficult in an enterprise environment. This means that the more devices connected without proper security, the greater the risk of breaches. When you consider the fact that most of these devices are connected to the corporate network, the probability of a major breach increases.
Why IoT Security Matters
Attackers frequently use IoT devices to gain unauthorized access into enterprise networks. The security features of many IoT devices are insufficient when compared to traditional IT systems which leaves them vulnerable to exploitation. The compromise of one IoT device can trigger data breaches and operational failures or cause physical damage in vital sectors like healthcare and manufacturing.
Businesses need to put IoT security at the top of their list to protect their sensitive information and ensure compliance while defending their reputation. IoT penetration testing serves as an essential strategy for recognizing and managing vulnerabilities in IoT devices.
What is IoT Penetration Testing?
IoT penetration testing represents a focused security evaluation which examines the security of IoT devices alongside their networks and connected systems. This process tests real-world attack scenarios to reveal exploitable weaknesses in IoT systems. By conducting IoT pentests, enterprises can:
- Look for vulnerabilities in both device firmware and software as well as communication protocols.
- Evaluate how well encryption and authentication solutions perform
- Assess the security of applications running on mobile devices that connect to IoT systems
- Examine cloud-based applications that interface with IoT technologies.

- Ensure compliance with industry standards and regulations.
Common IoT Vulnerabilities
A variety of security problems afflict IoT devices because they suffer from substandard design practices alongside inadequate updates and testing procedures. The following list details several typical security vulnerabilities found in IoT devices.
- Default Passwords: IoT devices frequently come with preset weak passwords or hardcoded credentials that anyone can easily guess or find online.
- Lack of Encryption: Data sent between devices and servers frequently remains unencrypted which allows attackers to intercept it.
- Insecure Firmware: Attackers can exploit vulnerabilities present in outdated or poorly designed firmware.
- Weak Authentication: Some devices fail to implement multi-factor authentication (MFA) while others depend on inadequate authentication methods.
- Insecure APIs: IoT device communication APIs frequently lack proper security measures which results in unauthorized access to those systems.
- Physical Security Issues: The deployment of IoT devices in unprotected areas exposes them to risks from physical tampering.
- Insufficient Update Mechanisms: If IoT devices cannot accept security updates they remain at risk from unpatched vulnerabilities.
Why Choose Invicta Solutions Group?
Invicta pentesters bring expertise in PCI DSS compliance, including segmentation testing, a critical requirement for assessing IoT devices. Our team also specializes in securing IoT devices in healthcare facilities, where they often act as entry points to corporate networks containing electronic Protected Health Information (ePHI). With hands-on experience in high-stakes environments, Invicta ensures robust IoT security tailored to industry-specific needs.












