By Val Vask, Cybersecurity Expert
The other day, I was approached about penetration testing Azure. Having successfully completed an AWS penetration test, my colleague explained how an Azure penetration test shouldn't be much of a jump from AWS. Even more concerning was his preconceived notion that penetration testing Azure AD, which is now called Entra ID (but more on that later), is almost the same as attacking an Active Directory environment.
These misconceptions are not singular or unique to just my coworkers, but commonly held beliefs by many people unfamiliar with the differences between Azure and AWS. Furthermore, the name Azure AD was changed in order for people to not conflate Azure's Identity & Access Management (IAM) with on-prem Active Directory.
What follows is an explanation of why Microsoft changed the name of its IAM nomenclature from Azure AD to Entra ID, what the differences are between on-prem AD and Azure Entra ID, and a few of the differences between Azure penetration testing and AWS penetration testing.
Why the Change from Azure AD to Entra ID?
Azure Active Directory was renamed to Entra ID to help clarify its distinct role in identity management and reduce confusion with on-premises Active Directory. Unlike on-prem AD, Entra ID is cloud-native, designed specifically for managing identities and access in a cloud context. Its renaming to Entra ID emphasizes its unique purpose: managing cloud-based resources and users, supporting applications beyond just Microsoft, and extending security features like conditional access, multifactor authentication, and user-specific risk scoring.
Key Differences Between On-Prem Active Directory and Entra ID - A Simplified Comparison Chart

Common Misconceptions About Cloud vs. On-Prem Penetration Testing
Cloud Infrastructure Is Similar to On-Prem Environments: While cloud infrastructure does share some foundational elements with on-prem environments, they are distinct in architecture, access control, and security models. For example, with Azure, identity management centers on Entra ID, a cloud-native directory that interacts with Azure resources in a way that on-prem AD does not. This can mean a higher focus on misconfigured permissions, insecure configurations, or API security, areas that differ significantly from traditional AD penetration testing.
Cloud Penetration Testing Equals Server/Network Testing: In on-prem pentesting, the focus might be on network-level attacks, open ports, or physical hardware vulnerabilities. However, cloud pentesting emphasizes securing cloud permissions, IAM roles, configuration mismanagement, and services like managed databases and serverless functions. Azure and AWS offer different sets of services and, subsequently, have unique security configurations and attack surfaces.
Azure Pentesting vs. AWS Pentesting
Azure and AWS both provide highly flexible cloud services, but their penetration testing methodologies differ due to their unique configurations, IAM structures, and service offerings.
IAM Structure and Identity Management: Azure leverages Entra ID, which is tightly integrated into Microsoft's ecosystem. Entra ID emphasizes identity governance, conditional access, and multifactor authentication. AWS uses IAM, which focuses on role-based access control for managing permissions across AWS resources. Due to Azure’s deeper integration with Microsoft products, pentesters often encounter complexities around permissions, especially when working with legacy or hybrid Azure environments.
Configuration Models: In AWS, configuration missteps in IAM roles, bucket policies, and security groups often pose risks. In Azure, the focus includes configuring Azure roles, resource groups, and networks, and often involves complex network segmentation and identity management specific to Azure environments.
Service Offerings and Attack Surface: While both AWS and Azure offer services like storage, compute, and database management, each has unique services that require different approaches. For instance, Azure's platform includes many native integrations with Microsoft tools (like Office 365), which bring in different attack vectors, such as the possibility of privilege escalation through misconfigured access in Office services or PowerShell endpoints.
So, Why Pentest Azure?
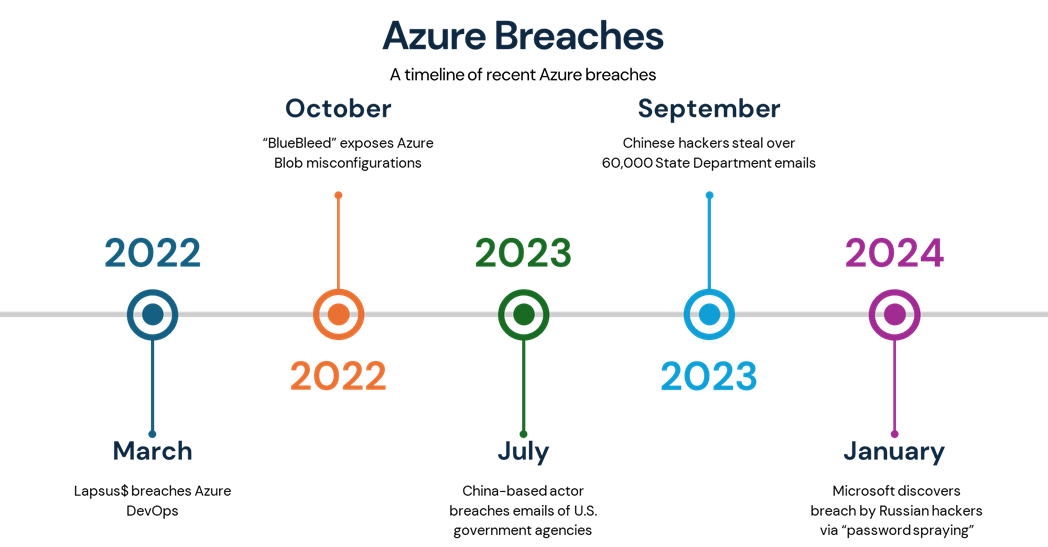
Recent high-profile breaches of Azure infrastructure tell a story of how hackers are increasingly targeting Azure—and with good reason. As the second-largest cloud provider, Azure commands a considerable market share, making it a tempting target for adversaries. Some may argue that an Azure penetration test is more of an “audit,” but at Invicta Solutions Group, we take it a step further. By actively exploiting discovered vulnerabilities, we’re able to demonstrate the true impact of misconfigurations or overly permissive roles present in our clients' Azure environments. This approach not only identifies vulnerabilities but also highlights their potential real-world consequences, empowering clients to secure their cloud infrastructure with confidence.
Final Thoughts
Understanding the nuances between Azure and AWS penetration testing not only improves security posture but also avoids common pitfalls due to assumptions about how cloud services mimic traditional on-premises environments. While they share overarching cloud security principles, each cloud provider has its architecture, IAM structure, and security considerations, making it essential to approach each cloud provider as its own unique ecosystem.












